[ad_1]

The new announcement that Activision Blizzard acquired King Digital Leisure, maker of the hit activity Sweet Crush, for a staggering $five.9 billion is an acknowledgement of the promising (and profitable) long term of cell games.
The world wide gaming industry is projected to get to $91.five billion in 2015. Though Pc and console games are however mainstream, cell is the quickest rising segment — escalating 21 p.c year-in excess of-year — thanks to the penetration of smartphones in emerging markets and the profitable “freemium” revenue model of cost-free-to-play games with in-application purchases. Reviews exhibit that customers are quick to shell out cash for VIP position, virtual goods to raise activity play or even to earn the activity at an ordinary paying of $50 for every consumer for every activity.

Graphic resource: Newzoo, World-wide Online games Marketplace Report 2015
With the industry booming so favorable, it is not surprising that online criminals have also uncovered their way into the ecosystem and are building a thriving underground industry for in-activity virtual items. How do they pull this off? Here are a couple of assault approaches we’ve noticed in the wild.
Sybil attacks by means of proxy servers
Proxy servers rented out by cloud companies permit online criminals to drastically scale up their operations and bypass status-primarily based detection programs. In the context of cell activity fraud, they also permit attackers to assume numerous fake identities by simulating presence in various geographic destinations, depending on in which the servers are located.
These fake identities (or “Sybils” as they are regarded in peer-to-peer networks) are leveraged to get gain of activity promotions for rare or minimal virtual goods, these types of as all those that are only presented in particular locations or in minimal everyday quantities.
They are also employed to accomplish virtual forex arbitrage: By simulating presence in various nations around the world, the attacker can buy virtual items in one place (the one with the weaker forex), resell them at an additional place (the one with the stronger forex) and pocket the selling price variance.

The attacker routes visitors by way of an abroad proxy server to simulate presence in an additional geographic place (one), buy virtual goods from the activity application (2) and resell to players for a income (3).
These “proxy” servers in various networks and locations are not minimal to hosts rented out by cloud companies and web hosting suppliers. Attackers also exploit compromised equipment located in households or business enterprise DSL networks, these types of that the malicious activities look identical to (or intermixed with) all those from benign customers.
In-application buy brokers
Some cell games do not permit virtual goods to be transferred between gamers. In this case, the goods cannot be ordered in advance to be resold at a later on time, as in the previously mentioned illustration.
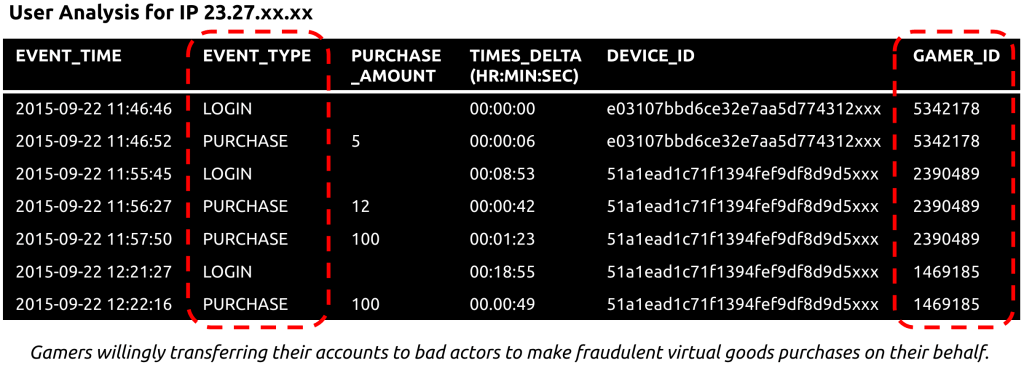
Not to be defeated, online criminals get a various technique with these sorts of games and virtual merchandise marketplaces. They will advertise selling price discounts so irresistible — at 25 p.c off, or a lot more — that gamers hand in excess of their activity application login credentials to have an individual else buy the virtual goods on their behalf. The sellers will even remind you to modify your password right after the transaction is accomplished to “avoid unnecessary issues.”

Guidance from sellers on the underground industry for cell activity gamers hunting to buy affordable virtual items.
The table down below exhibits an illustration of this assault in action. Just about every row corresponds to an function logged by the cell activity application. We can see this attacker consistently log on as various customers (gamer IDs) to make purchases, without having producing any other sorts of gatherings indicative of true activity play. In fact, every single consumer is only logged in for at most a couple of minutes — until the purchases are entire.
Faux or stolen credit cards
No one would threat currently being in this business enterprise if the fork out-off wasn’t good, so how can the underground industry present these types of steep discounts? It is again to the resource of significantly financial fraud and head aches in new several years — counterfeit or stolen credit cards from knowledge breaches.
In contrast to in-store purchases that can be safeguarded by EMV chip-and-pin engineering, activity application builders have very minimal methods by which to confirm an in-application, card-not-existing transaction. Present methods have a tendency to count on rules-primarily based programs or supervised mastering versions, which can only respond to regarded assault patterns.
To make items a lot more complicated, in-application transactions are frequently mediated by cell payment platforms, these types of as Apple App Retail outlet or Android Shell out, so apps lack visibility into facts of the transactions for distinguishing between reputable and fraudulent purchases.
The real cost of in-application buy fraud
Why does all of this make a difference to cell games? Yes, virtual goods really do not genuinely “cost” everything, but this in essence implies that there is a massive amount of cash dropped to unrealized gains. It is estimated that for just about every reputable virtual merchandise sold and downloaded, there are 7.five virtual merchandise downloads dropped to fraud. This amount can be significantly greater in some nations around the world — in China, for illustration, there are 273 fraudulent virtual goods downloaded for just about every reputable merchandise. This implies a staggering 50-ninety nine p.c of all virtual good purchases are illegitimate.

But maybe the major issue for games is the detrimental impact on consumer expertise. When fraudulent in-application purchases pollute the economics of the activity and permit some gamers to get an unfair gain, it ruins the expertise for other gamers. With the gaming landscape currently being as aggressive as it is nowadays, most gamers won’t put up with this, and games cannot find the money for to drop customers.
These are only a handful of assault approaches faced by cell gaming apps, and the complete listing is not only significantly for a longer time, but also continually transforming to evade present detection methods. As cell apps count a lot more and a lot more on in-application “virtual” purchases, they need to also be completely ready to fight fraud. There is a true price affiliated with dropped virtual items, and one that has massive detrimental impact on both of those consumer advancement and organization income.
Featured Graphic: La Gorda/Shutterstock
Study Extra Here
[ad_2]
There Is Actual Fraud In The Underground Marketplace For In-Match Virtual Products
No comments:
Post a Comment